Good day, all.
Please can I get some help?
As per the latest ISO compliance regulations our customers have to prove
- All user accounts that have the “System Administrator” server role
- All user accounts with administrator rights are in a vault.
Basically what I would love to be able to pull a detailed pillaged access or permissions report, I am working with multiple vaults 10+ and hundreds of users. What I want to avoid is going user by user to get this information like the below screenshot.
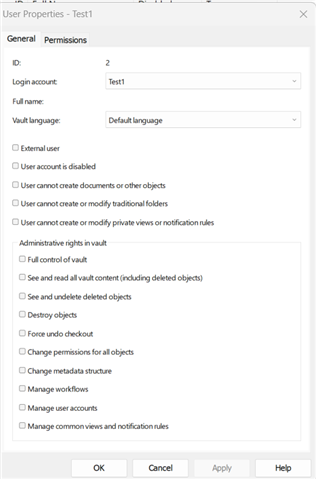
Basically something like this or as close to it as possible without putting undue workload onto the client or auditors.
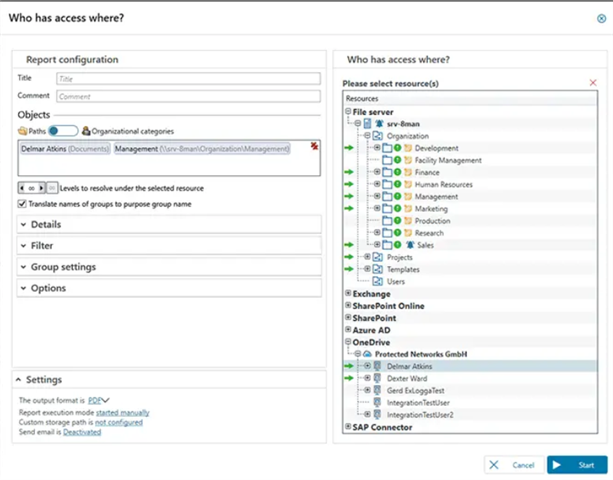
Or like this any ideas are most welcome!
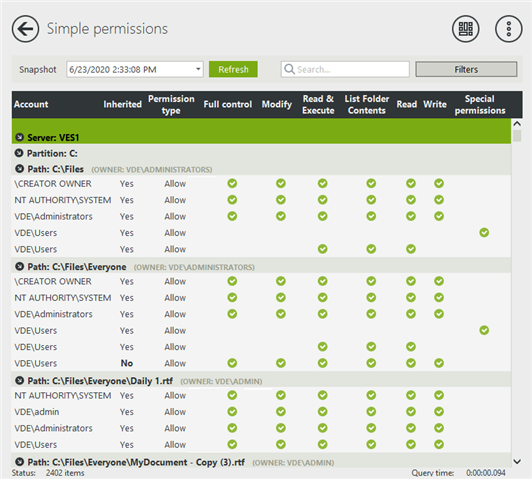
Kind Regards

